In brief
- A whitehat hacker discovered a vulnerability in an Ethereum smart contract that put nearly $10 million in ETH at risk.
- Overnight, a rescue team was organized to bring the funds out of harm's way.
- The effort united a team of blockchain security experts and miners from around the world.
A blockchain security researcher and whitehat hacker, known as samczsun, today published a detailed “post mortem” of an undercover operation that resulted in the rescue of 25,000 ETH, worth over $9.6 million at the time. The funds were saved from a vulnerable Ethereum smart contract.
How do you rescue 10 million dollars from a vulnerable smart contract without letting attackers know it’s there? Last Tuesday, @epheph, @sparkpool_eth, @tzhen, @wadealexc, and I found out.https://t.co/WOjO651VIw
— samczsun (@samczsun) September 24, 2020
On September 15, samczsun was looking through Ethereum smart contracts in search of vulnerabilities (like he often does). Eventually, he discovered what later turned out to be a part of Lien Finance’s protocol: a smart contract that contained over 25,000 ETH.
Only these funds could’ve been taken by anyone.
According to the post, the smart contract contained a “burn” function. Essentially, this allowed any users to mint themselves a lot of valueless tokens and exchange them for all the ETH stored on the contract, getting away with a cache worth nearly $10 million. For DeFi’s sake, Samczsun decided to intervene.
Since Lien Finance’s team was anonymous, the whitehat went through a bunch of potential connections to anyone involved. Alexander Wade, a security researcher at ConsenSys—one of the two companies that audited the smart contract (and also funds an editorially independent Decrypt)—and Ethereum security specialist Scott Bigelow soon joined the rescue operation.
Realistically, there were two ways the situation could’ve been resolved. First, Lien Finance could’ve publicly disclosed the vulnerability, but that would’ve created a perfect opportunity for hackers to snatch the funds—like placing a “free money” sign.

Second, the whitehat team could’ve exploited the smart contract itself and then return the funds to their rightful owners. But this would’ve definitely attracted the so-called generalized frontrunner bots—apex predators of Ethereum’s mempool.
The mempool, expressively referred to as “Ethereum’s Dark Forest,” is a special “staging area” where transactions congregate before they are accepted by miners to be included in the next block. And this area is constantly patrolled by frontrunners—special bots that are looking for any exploitable transactions to hijack.
Basically, frontrunners could automatically copy any transaction in the mempool, replace its addresses with their own and make sure that the duplicate operation gets picked up by miners first. In the current situation, that meant $10 million could’ve been easily stolen by frontrunners in a matter of seconds. Secrecy was essential.
With the help of blockchain researcher Tina Zhen, the team added members of both CertiK—the second company that audited the smart contract—and Ethereum mining pool SparkPool to the rescue effort, as well as finally reaching out to Lien Finance.
After a short onboarding, SparkPool’s coders spent the next couple of hours developing and testing a specialized “whitehat API” that would allow miners to pick up a transaction without displaying it in the mempool. In their turn, members of the whitehat team finished the script to generate four sequential signed transactions that would ultimately save the 25,000 ETH.
But these transactions weren’t designed to directly withdraw the funds. If executed in the correct order, they would transfer 30,000 SBT and LBT tokens—which are infinitely mintable—to Lien Finance, allowing it to convert these tokens back into ETH via the burn function with the final operation.
When all preparations were complete, the whitehat team finally commenced the rescue operation. By working with a mining company, the transactions successfully evaded the bots. This is because the transactions were not sent to the mempool—they were directly placed in a block by the miners themselves.
“After adapting the transaction-creation script to feed the transactions directly to SparkPool’s new endpoint, it was time. I hesitated for a moment, but this was absolutely our best effort. We might lose $9.6M, but there would be no regrets,” the post explained, adding, “The ~15 blocks it took before our transactions were included felt like hours, but finally, we had our immaculate transactions: mined, in order, not reverted.”
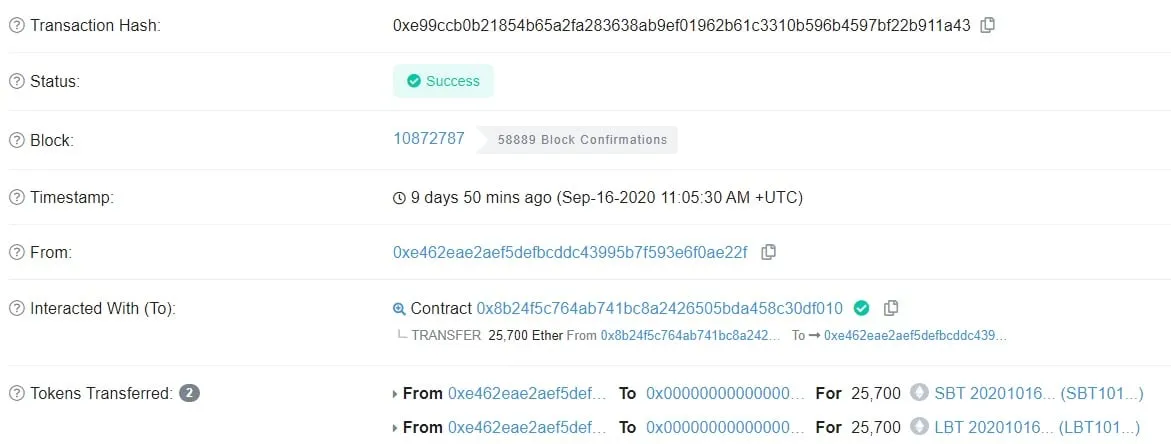
Now, what was left was for the Lien Finance team to exchange the SBT and LBT tokens for ETH using the burn function. A few moments after the final transaction was executed, Etherscan reported its successful completion, sweeping 25,000 ETH out of harm’s way.
Thus, the whitehat team “escaped the dark forest,” and saved a small fortune.

