In brief
- Researchers find a new malware threat named KryptoCibule.
- KryptoCibule steals your crypto, mines cryptocurrency using your computer power, and redirects any incoming payments to a hacker address.
- The malware hides within pirated torrent files.
Security researchers have unearthed a new strain of malware dubbed KryptoCibule—and it specifically targets cryptocurrency enthusiasts.
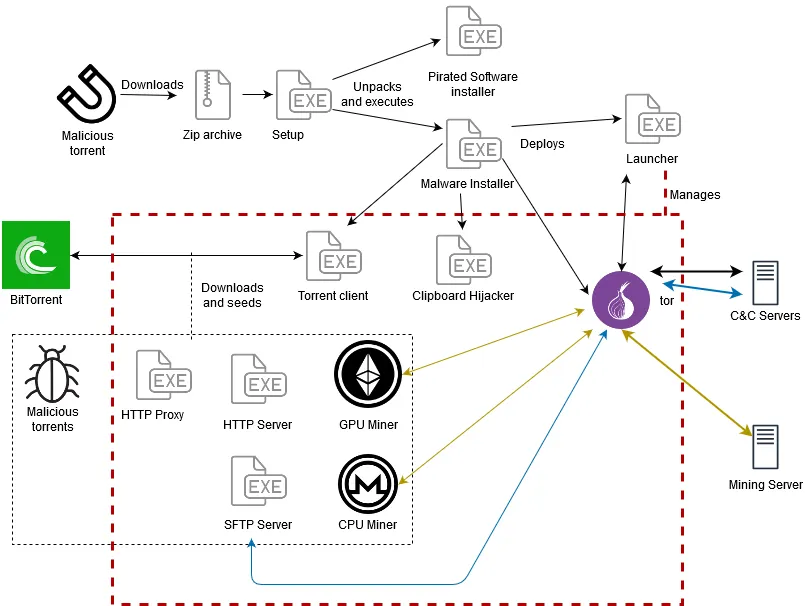
According to a report from Cyber-security firm ESET, KryptoCibule represents a triple threat for crypto holders.
First, the malicious software installs a miner for a process known as cryptojacking, a method that harnesses the victim's computing power to mine cryptocurrencies on the hacker's behalf. It then steals any files related to cryptocurrency wallets, wiping the victim clean of any stored crypto funds. To top it off, the malware replaces the victim's wallet addresses, redirecting them to hijack any incoming payments.
The beauty—or perhaps more appropriately, threat—of KryptoCibule, is its multifaceted attack vectors. Even if a victim doesn't hold any cryptocurrency, bad actors can still gain from the cryptojacking element.
The very first instance of KryptoCibule apparently stretches back to 2018, where it was little more than a simple Monero-based cryptojacker. Since then, the malware has evolved, updating to integrate the aforementioned functionality as well as an Ethereum-based crypto miner, and the ability to auto-update via BitTorrent.
Per ESET, KryptoCibule is typically spread through pirated torrent files. Thinking they've scored a free version of some ill-gotten software, victims unwittingly install the malware—exposing themselves, their computer, and any potential cryptocurrencies.
The majority of the malware-infected torrents apparently originated from uloz.to, a torrenting site popular in the Czech Republic and Slovakia. As such, distribution seems to be limited to the two countries—for now, at least. Still, that's no guarantee that it'll remain that way.

