In brief
- A leaked INTERPOL manual on dark web markets trading in chemical and biological weapons includes advice for transacting in and seizing cryptocurrencies.
- The manual coaches law enforcement on how to seize cryptocurrency that is suspected to be tainted by crime.
- The document was leaked by Anonymous as part of the 270GB "Blueleaks" data dump.
A leaked INTERPOL manual covering the trade in chemical and biological weapons on the dark web includes advice for transacting in and seizing cryptocurrencies.

The manual, titled ‘Investigating Biological and Chemical Terrorism on the Darknet’, coaches law enforcement on best practices for infiltrating the dark web’s contrabandist subcultures. As well as advising investigators on how to transact in cryptocurrency, it also explains how to create an undercover identity, use the Tor browser and access dark web community forums such as Dread.
Seizing dirty Bitcoin
The document coaches law enforcement on how to seize cryptocurrency that is suspected to be tainted by crime. To protect the integrity of INTERPOL’s investigative tradecraft, and to avoid a potential “Red Notice,” Decrypt is declining to publish these findings.
In general, however, because cryptocurrencies are inherently not sovereign money, they are not beholden to any mutual legal assistance treaty (MLAT). If police have control of a suspect’s wallet, they can transfer the money to a law-enforcement controlled account and no MLAT permission is required because no nation has dominion over it.
Still, the INTERPOL manual notes: “National legal frameworks and agency regulations related to Darknet access and investigations can differ from one country to another and must always be respected.”
The manual also offers tutorials on how to operate virtual private networks (VPNs), work in virtual machine environments such as Whonix, and communicate covertly via messages ciphered with pretty-good-privacy (PGP) encryption.
Project Pandora and bioterrorism
The manual, published in 2019 and spanning 142 pages, was created in support of INTERPOL’s Project Pandora, a 2018 initiative focused on “countering biological and chemical trade via the Darknet through the development of investigative and operational countermeasures.”
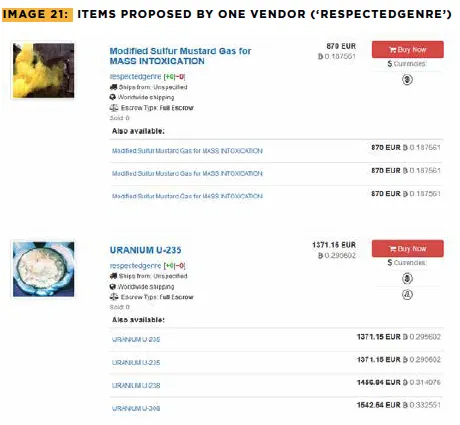
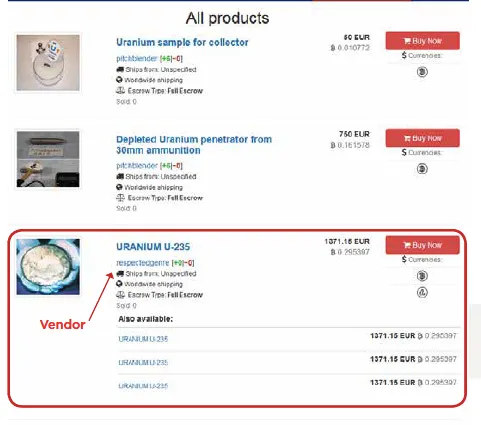
The manual includes screencaps purporting to show Uranium and mustard gas that were scraped from the now-defunct darknet market, Berlusconi, which was seized by Italian authorities last November.
Growing international scrutiny of this dangerous trade comes at a time when law enforcement is increasingly encountering cases where people are discussing, or actually attempting to purchase, bacterial and chemical agents on the dark web—using cryptocurrency as a medium of exchange.
In July 2015, Liverpool, UK resident Mohammed Ali was convicted after attempting to buy 500mg of ricin from an undercover FBI agent, using Bitcoin. The judge presiding over Ali’s case said there was “no evidence that he was planning any sort of terrorist attack.”
Last September, Oakland resident Samford “Bemi” Faison was sentenced to almost six years in jail for paying $95 in Bitcoin to an undercover FBI agent, in a bid to acquire a toxic chemical to kill his estranged wife. The former child actor authored a public post on a dark web forum openly soliciting chemicals; it was discovered by FBI agents, who then orchestrated a sting operation.
FBI undercover agents nabbed another would-be dark web chemical-weapon buyer last March, when they arrested 37-year-old Sijie Liu of Winnipeg, Canada in Pembina, North Dakota. Liu was arrested after placing an order for 10 milliliters of toxin and protective equipment to handle it; the package was recovered at a commercial mail receiving facility. She was sentenced to six years in US prison at the end of last month.
Are biological and chemical weapons for sale on the dark web?
The above cases notwithstanding, experts who spoke to Decrypt are skeptical that there’s a widespread market for biological and chemical weapons on the dark web. Madeleine Kennedy, a spokesperson for blockchain investigation and compliance firm Chainalysis, told Decrypt, “We have not seen much on the dark web related to chemical and biological weapons and suspect most listings of that nature are scams.”
Scott Stewart, vice president at protective intelligence firm TorchStone Global, and a former US Army intelligence officer and special agent for the State Department’s Diplomatic Security Service, is similarly doubtful that a significant attack could be carried out using chemical or biological materials obtained from the dark web.
“A serious and sophisticated chemical or biological weapons program by an actor like the Al-Qaeda or ISIS would not be online at all. They know that is terrible OpSec (operational security) even on the dark web or using encrypted channels or devices,” he told Decrypt.
More likely, he suggested, is that someone from a core group could communicate with a grassroots supporter using the dark web, ordering them to perform a terrorist attack. “But instead of telling them to use a knife, gun, or vehicle, they'd be instructing them to weaponize the chemical agent or disease,” he added.
In the wake of the coronavirus pandemic, however, biological terrorism is increasingly on the authorities’ radar. In April this year, UN Secretary-General António Guterres noted that COVID-19 could embolden threat groups to pursue pathogen-based attacks.
How did the INTERPOL manual leak?
An INTERPOL spokesperson told Decrypt that the agency “works with law enforcement and other global experts to develop manuals and handbooks on a wide variety of crime types.”
“Such handbooks typically provide information on best practices, case studies, and the latest investigative tools and techniques,” the spokesperson said. “These are made available to law enforcement investigators via the INTERPOL National Central Bureaus in each member country.”
The INTERPOL manual was one of a cache of law enforcement documents, dubbed Blueleaks, which were acquired by hacktivist group Anonymous via a security breach at law enforcement web-hosting firm Netsential.
Originally posted online by “transparency collective” Distributed Denial of Secrets, the 270GB data dump reveals the inner workings of over 200 US police departments, including the techniques used by the FBI to track Bitcoin laundering on the dark web. German authorities seized DDoS’ public data servers on July 2, but their website is still online.





